Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Edge, Cloud, Hybrid, Virtual, Bare‑metal, or Multi-cloud? Deciding On Your Perfect Kubernetes Architecture
Choosing the right Kubernetes architecture is no longer about picking a single environment. From cloud and edge to hybrid, bare-metal, and multicloud setups, each option offers unique benefits and challenges. This article by Ben Radstone explores six key Kubernetes deployment models, comparing their pros, cons, and ideal use cases to help organizations design flexible, resilient, and cost-efficient infrastructures for modern workloads.
Format: ArticleTopic: Software/ ToolsContent Type: Community Content -
Effortless SBOM Analysis: How Anchore Enterprise Simplifies Integration
As software supply chain security becomes a top priority, organizations are turning to Software Bill of Materials (SBOM) generation and analysis to gain visibility into the composition of their software and supply chain dependencies in order to reduce risk.
-
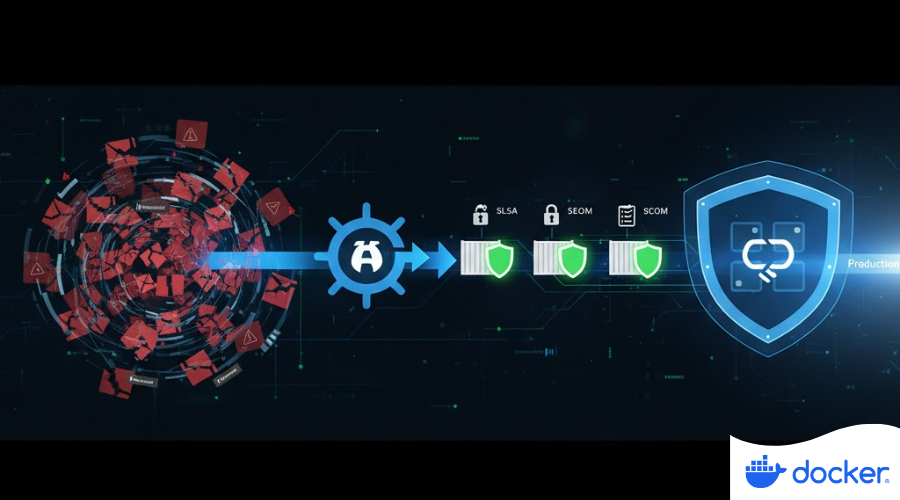
Expanding Docker Hardened Images: Secure Helm Charts for Deployments
Docker is simplifying Kubernetes security! Discover how new Helm charts in the Docker Hardened Images (DHI) Catalog give users a secure, compliance-ready alternative after the Broadcom/Bitnami changes. Deploy DHI by default, ensuring SLSA Level 3 security and SLA-backed patching for every Kubernetes workload.
Format: ArticleTopic: Software/ ToolsContent Type: Community Content -
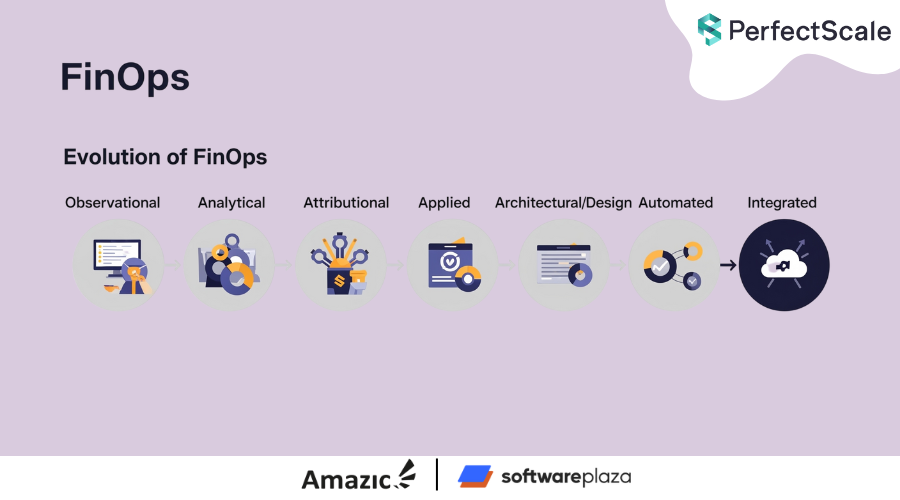
FinOps in 2025: The 6 Phases of FinOps Evolution
Explore the six evolving phases of FinOps, from the initial "Observational" data collection to "Automated" and the future of "Integrated FinOps," revealing how organizations learn to manage cloud spend and optimize infrastructure efficiently over time.
-
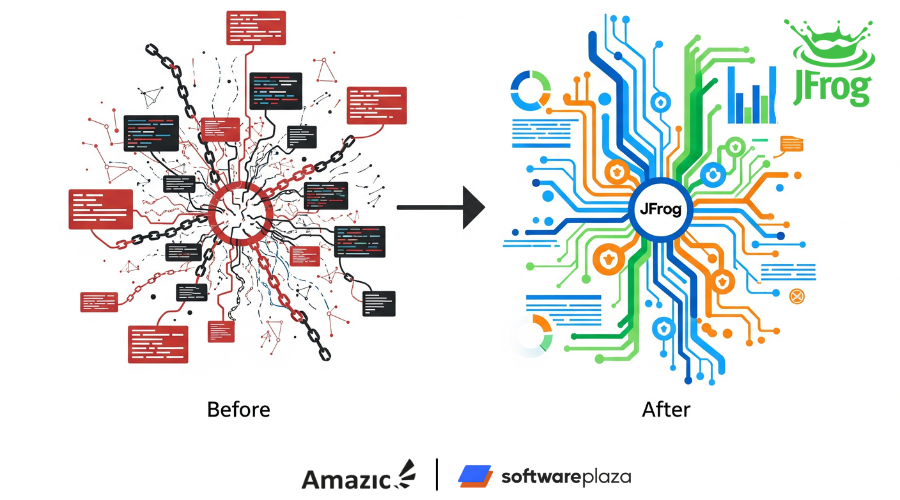
Fintech Company Streamlines Software Supply Chain Management for Enhanced Security
This leading financial services technology company has significantly improved auditability and traceability, streamlined its security technology tool stack, and strengthened its end-to-end software supply chain security by adopting JFrog Advanced Security.
-
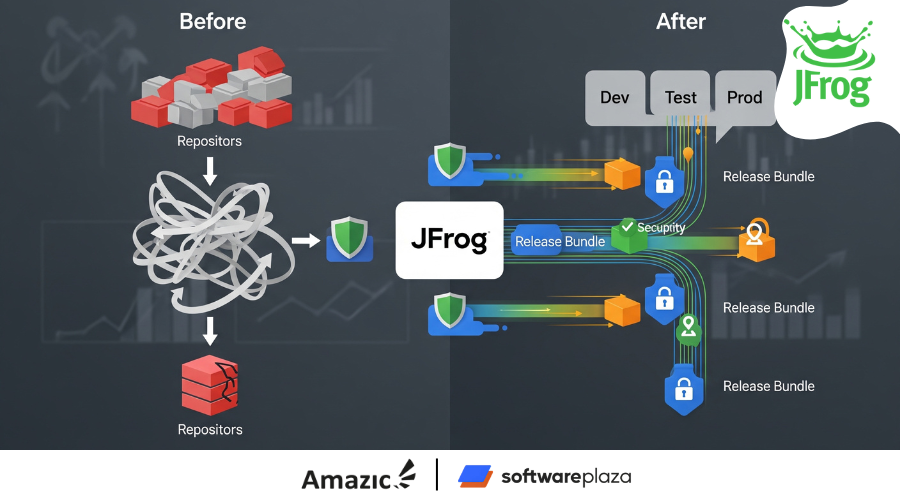
Fintech Developer Streamlines Software Production with JFrog’s Release Lifecycle Management
A multinational financial technology firm improved security and compliance by adopting the JFrog Platform for software releases. Using immutable release bundles and controlled promotion, they minimized risks while maintaining strict regulatory standards. JFrog’s Release Lifecycle Management (RLM) capabilities reduced manual intervention, allowing teams to focus on innovation.
-
Five Cloud Mistakes Holding Your Fintech Back
Is your cloud bill a sneak attack? Discover the 5 Cloud Mistakes—from ignoring security compliance (POPIA/FSCA) to letting multi-cloud turn into a "digital spiderweb"—that are crippling South African fintechs. Learn the Kinetic Skunk tips for fixing legacy debt and achieving predictable growth.
Format: ArticleTopic: Best PracticesContent Type: Community Content -
Five Reasons Standalone Vulnerability Scanning Isn’t Enough in 2025
Vulnerability scanning alone doesn’t cut it anymore. While it’s long been a core security practice, scanning tools can’t tell you which vulnerabilities are exploitable, how attackers would target them, or which ones pose real risk. This article explores the limitations of vulnerability scanning, the shortfalls of traditional vulnerability management, and why organizations must adopt a risk-based, context-driven approach to application security. Learn how to prioritize based on exploitability, integrate security across the SDLC, and move toward continuous, intelligent threat detection.
-
Five ways to transform document translation with DeepL Translator
Transform your document workflow with DeepL Translator! Discover 5 ways to get high-quality, formatted translations fast. From dropping PDFs without OCR to applying glossaries for brand consistency and editing translations with full control, learn how DeepL saves businesses like Panasonic and JAE time, money, and costly mistakes.
-
From Alerts to Actions: Turning AppSec Data into Business Value
Modern AppSec teams are overwhelmed with alerts but still struggle to answer the one question that matters: What should we fix first? This article explores how shifting from raw data to contextual insights helps prioritize the most impactful vulnerabilities, align security efforts with business goals, and move application security from a cost center to a strategic enabler.
-
GitKraken Desktop 11.2: Merge Conflicts, Meet AI (and More Dev-Quality-of-Life Wins)
Tired of merge conflict headaches? Discover GitKraken Desktop 11.2, where AI-powered assistance simplifies conflict resolution with context-aware suggestions and confidence levels. Plus, enjoy new quality-of-life wins like hunk-level reverts, enhanced collaboration features, and CLI support for AI agents, supercharging your Git workflow!
-
GitLab Duo Agent Platform Public Beta: Next-gen AI orchestration and more
Experience the future of DevSecOps with the GitLab Duo Agent Platform! Now in public beta, this next-gen platform lets developers collaborate with AI agents to automate routine tasks, streamline complex workflows, and focus on innovation. Discover how it’s designed to transform the entire software development lifecycle.