Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
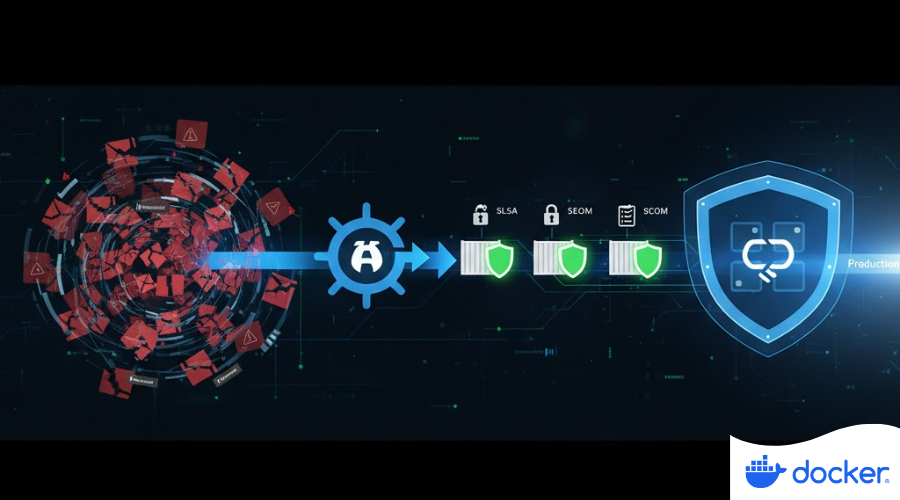
Docker Hardened Images: crafted by humans, protected by AI
Docker’s Hardened Images (DHI) are secured by a dual approach: human expertise backed by AI. Discover how Docker’s internal AI guardrail spotted a critical logic flaw in an nginx-exporter update, blocked the release, and contributed the fix upstream, proving AI is the best force multiplier for security architects
Format: ArticleTopic: Software/ ToolsContent Type: Editorial Content -
Expanding Docker Hardened Images: Secure Helm Charts for Deployments
Docker is simplifying Kubernetes security! Discover how new Helm charts in the Docker Hardened Images (DHI) Catalog give users a secure, compliance-ready alternative after the Broadcom/Bitnami changes. Deploy DHI by default, ensuring SLSA Level 3 security and SLA-backed patching for every Kubernetes workload.
Format: ArticleTopic: Software/ ToolsContent Type: Community Content -
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.
Format: ArticleTopic: Software/ ToolsContent Type: Community Content -
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
Format: ArticleTopic: Best PracticesContent Type: Community Content -
How IBM Instana uses Teleport to manage access to their cloud infrastructure
IBM Instana needed to secure access to its sensitive cloud infrastructure while boosting developer agility. Discover why they chose Teleport to replace VPNs and shared credentials, simplifying compliance audits (SOC 2, FedRAMP) and eliminating management overhead across their rapidly scaling, multi-cloud environment.
Format: ArticleTopic: Best PracticesContent Type: Case Study -
Rush Street Interactive Levels Up Cloud Security with Teleport
Online gaming leader Rush Street Interactive (RSI) chose Teleport to eliminate security friction across its multi-cloud infrastructure. Discover how Teleport delivered 3x faster access provisioning, eliminated inbound SSH ports via reverse tunnels, and secured SOC 2 Type 2 compliance by leveraging short-lived credentials for human and machine identities.
Format: ArticleTopic: Best PracticesContent Type: Case Study